[High Resolution] Why Can Spear Phishing Be So Dangerous
Why can spear phishing be so dangerous - Spear phishing is a tactic used by cyber criminals whereby they attempt to attack a specific individual as a conduit into the organization. Up to 30 cash back Spear phishing attacks are designed to appear like legitimate emails from familiar or well-known sources. This phishing tactic learns of the victims personal information and uses it. Spear phishing is a type of phishing but more targeted. Spear phishing attempts use your emotions to their advantage. Zero-day vulnerabilities are unknown software flaws in browsers desktop applications and plug-ins. With even a little bit of information on the targeted user cybercriminals are able to easily pose and spoof as a trusted entity and even craft bodies of emails that will more likely entice a user to respond. Instead they aim to access sensitive company data and trade secrets. Recent high profile data breaches such as. Cybersecurity and its nature are constantly changing and several kinds of threats are evolving every now and.
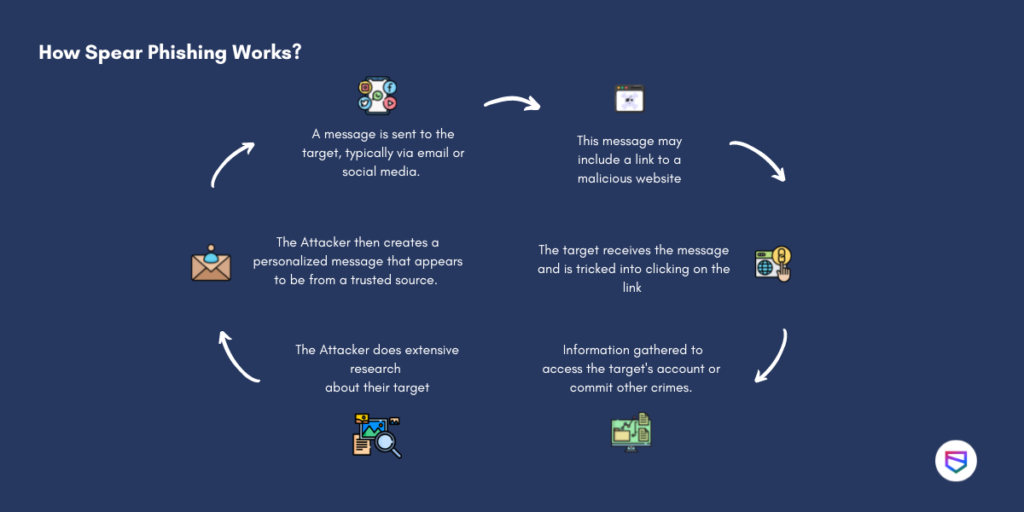
The practice of hacking into someones system through emails shared through an already known contact of a person is known as spear phishing. The personal info gathered helps the attacker disguise themselves and create an authentic-looking message that appears to come from a trusted. Most phishing schemes are somewhat random and they can do damage. Spear-phishing attackers methodically target a victim to use them as a way into an organization or for stealing information while a phishing actor does not bother who their target is. Again phone scams offer a great illustration. Spear phishing requires more preparation and time to achieve success than a phishing attack. According to CSO spear phishing attacks can be broken down into three main steps. This is because spear phishing has a human touch. Spear Phishing Leverages Zero-Day Exploits. Spear phishing is more precise.
Spear Phishing One Of The Biggest Cybersecurity Threats
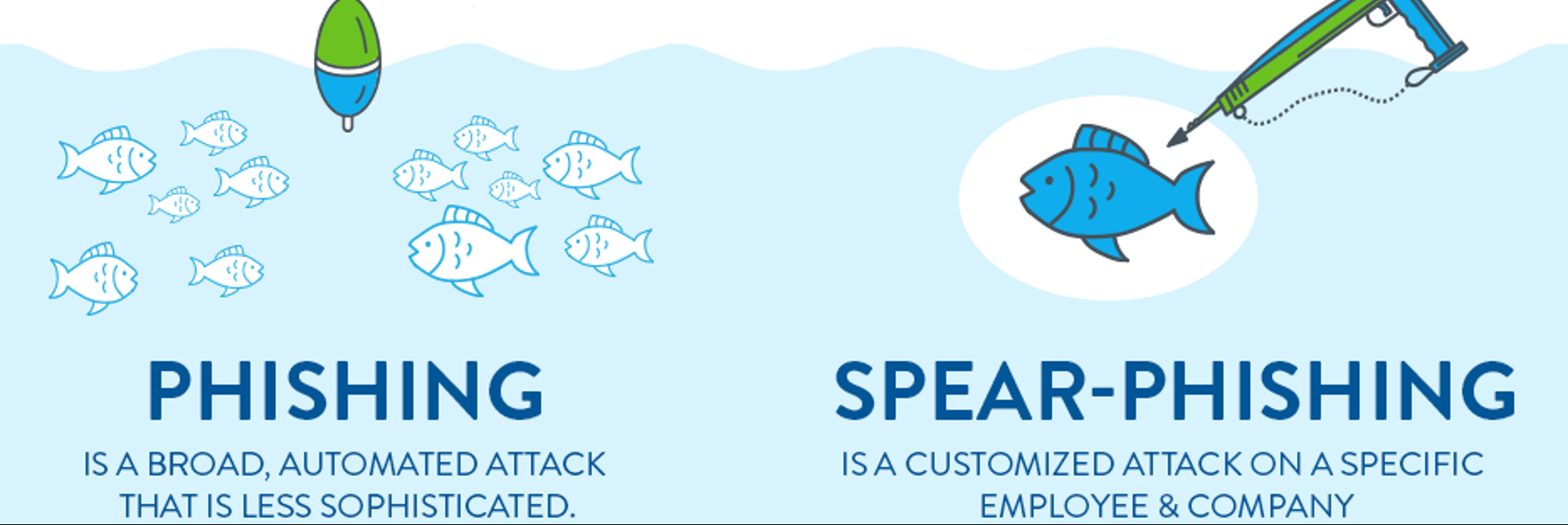
As with regular phishing cybercriminals try to trick people into handing over their credentials. Most phishing schemes are somewhat random and they can do damage. Infiltration This can be done by directing users to click on a malicious link that downloads and installs malware or leads them to a fraudulent website disguised as a. These emails include prompts to click on links and once you do youve potentially exposed yourself to malicious file downloads. According to CSO spear phishing attacks can be broken down into three main steps. Most early phishing was a mass attack the same email or recorded message sent to many people hoping to snag a minority of those contacted. What is phishing and how do I spot it. This can cause wide-ranging fraud and system security infiltration. Spear phishing is a type of phishing but more targeted. In contrast spear-phishing is more dangerous because it focuses on an individual with personalized information.
However the goal reaches farther than just financial details. With even a little bit of information on the targeted user cybercriminals are able to easily pose and spoof as a trusted entity and even craft bodies of emails that will more likely entice a user to respond. This increased level of an understanding around a users interests is exactly what makes spear phishing so dangerous. Spear-phishing attacks are often orchestrated in concert with business email compromise BEC attacks. Until they are fixed and patched they can be exploited by attackers to compromise systems and gain access to the network and other resources including personal and financial data.
Why Phishing Is More Dangerous Than Ever And How To Protect Yourself Ezcomputer Solutions
Why Is Spear Phishing So Dangerous. This can cause wide-ranging fraud and system security infiltration. Examples of phishing emails. Spear-phishing attacks are potentially the most harmful since there is commonly a financial motivation behind the attack and the financial losses can be extreme. Infiltration This can be done by directing users to click on a malicious link that downloads and installs malware or leads them to a fraudulent website disguised as a. Instead they aim to access sensitive company data and trade secrets. Spear-phishing attacks are often orchestrated in concert with business email compromise BEC attacks. Phishing attacks are easier to detect as they typically use more generic emails and are sent to large numbers of people. Spear phishing is more precise. The purpose of the attack is the same as with any phishing email to gain access to login or confidential information or to deliver malware but in this instance the attack is targeted.
The personal info gathered helps the attacker disguise themselves and create an authentic-looking message that appears to come from a trusted. In addition with spear phishing or whaling malicious actors have the luxury of being able to perform copious amounts of research reconnaissance on their targets before launching an attack. Spear phishing is a type of phishing but more targeted. They just want to steal as much information as possible or cause damage. According to CSO spear phishing attacks can be broken down into three main steps.
Why Is Phishing So Dangerous Southeastern Technical
Spear phishing attempts use your emotions to their advantage. What is phishing and how do I spot it. Up to 30 cash back Spear phishing attacks are designed to appear like legitimate emails from familiar or well-known sources. Instead they aim to access sensitive company data and trade secrets. Infiltration This can be done by directing users to click on a malicious link that downloads and installs malware or leads them to a fraudulent website disguised as a. Why Is Spear Phishing So Dangerous. In addition the practice of spear phishing is on the rise. This threat evolves and changes and when done correctly will blend in with a victims legitimate communications. Understanding And Avoiding Spear Phishing and Phishing Attacks. According to CSO spear phishing attacks can be broken down into three main steps.
A bad actor impersonates someone you trust in an effort to scam you or steal your information. Up to 10 cash back A spear phishing attack begins with an attacker identifying a specific target and researching personal details such as their employer friends hometown recent online purchases etc. Spear-phishing attacks are often orchestrated in concert with business email compromise BEC attacks. The familiar tone and content of a spear phishing message make it more difficult for the average user to detect heightening the threat level of this type of cyber attack. Personal information is used in spear-phishing attempts to construct convincing schemes.
Why Phishing Is More Dangerous Than Ever And How To Protect Yourself Ezcomputer Solutions
Spear phishing attempts use your emotions to their advantage. Infiltration This can be done by directing users to click on a malicious link that downloads and installs malware or leads them to a fraudulent website disguised as a. In addition the practice of spear phishing is on the rise. The familiar tone and content of a spear phishing message make it more difficult for the average user to detect heightening the threat level of this type of cyber attack. One way to safely verify a link is by right-clicking on it and using the Inspect tool to check where its supposed to go. The purpose of the attack is the same as with any phishing email to gain access to login or confidential information or to deliver malware but in this instance the attack is targeted. In contrast spear-phishing is more dangerous because it focuses on an individual with personalized information. Spear phishing attacks frequently rely on the delivery of malware via email. What is phishing and how do I spot it. Spear-phishing attacks are often orchestrated in concert with business email compromise BEC attacks.
Up to 10 cash back A spear phishing attack begins with an attacker identifying a specific target and researching personal details such as their employer friends hometown recent online purchases etc. The practice of hacking into someones system through emails shared through an already known contact of a person is known as spear phishing. Because unlike wide low-tech scams spear-phishing attacks are highly focused and well-researched theyre effective. Learn About the Most Pervasive Types of Phishing and Prevention. This increased level of an understanding around a users interests is exactly what makes spear phishing so dangerous.
Spearphishing Gw Information Security Blog
Cybersecurity and its nature are constantly changing and several kinds of threats are evolving every now and. As with regular phishing cybercriminals try to trick people into handing over their credentials. Understanding And Avoiding Spear Phishing and Phishing Attacks. Infiltration This can be done by directing users to click on a malicious link that downloads and installs malware or leads them to a fraudulent website disguised as a. With even a little bit of information on the targeted user cybercriminals are able to easily pose and spoof as a trusted entity and even craft bodies of emails that will more likely entice a user to respond. Phishing attacks are easier to detect as they typically use more generic emails and are sent to large numbers of people. This increased level of an understanding around a users interests is exactly what makes spear phishing so dangerous. Spear phishing attacks frequently rely on the delivery of malware via email. Examples of phishing emails. In addition with spear phishing or whaling malicious actors have the luxury of being able to perform copious amounts of research reconnaissance on their targets before launching an attack.
Because unlike wide low-tech scams spear-phishing attacks are highly focused and well-researched theyre effective. Learn About the Most Pervasive Types of Phishing and Prevention. Spear-phishing attacks are often orchestrated in concert with business email compromise BEC attacks. The purpose of the attack is the same as with any phishing email to gain access to login or confidential information or to deliver malware but in this instance the attack is targeted. But far more dangerous are whats called spear-phishing campaigns.
Spear Phishing A Highly Targeted Phishing Attempt Security Boulevard
After identifying a target individual or group like an organization or business an attacker crafts and sends a message usually via email purporting to come from a trusted and familiar source. Cybersecurity and its nature are constantly changing and several kinds of threats are evolving every now and. Again phone scams offer a great illustration. With even a little bit of information on the targeted user cybercriminals are able to easily pose and spoof as a trusted entity and even craft bodies of emails that will more likely entice a user to respond. Why is Spear-phishing the most harmful. In contrast spear-phishing is more dangerous because it focuses on an individual with personalized information. Spear phishing attempts use your emotions to their advantage. As with regular phishing cybercriminals try to trick people into handing over their credentials. Spear Phishing Leverages Zero-Day Exploits. Phishing attacks are easier to detect as they typically use more generic emails and are sent to large numbers of people.
This is because spear phishing has a human touch. This can cause wide-ranging fraud and system security infiltration. Zero-day vulnerabilities are unknown software flaws in browsers desktop applications and plug-ins. Most early phishing was a mass attack the same email or recorded message sent to many people hoping to snag a minority of those contacted. In addition with spear phishing or whaling malicious actors have the luxury of being able to perform copious amounts of research reconnaissance on their targets before launching an attack.
What Is Spear Phishing And Why Is It So Dangerous Eset Blog
Firstly you need to know what is spear phishing. Email-borne threats have always been a top priority for IT security but spear phishing is one of the fastest growing attacks. Personal information is used in spear-phishing attempts to construct convincing schemes. Up to 30 cash back Spear phishing attacks are designed to appear like legitimate emails from familiar or well-known sources. In addition the practice of spear phishing is on the rise. The practice of hacking into someones system through emails shared through an already known contact of a person is known as spear phishing. They just want to steal as much information as possible or cause damage. Up to 10 cash back A spear phishing attack begins with an attacker identifying a specific target and researching personal details such as their employer friends hometown recent online purchases etc. According to CSO spear phishing attacks can be broken down into three main steps. Scammers typically go after either an individual or business.
In addition with spear phishing or whaling malicious actors have the luxury of being able to perform copious amounts of research reconnaissance on their targets before launching an attack. Because of their hyper-targeted nature spear phishing can be even more dangerous than traditional phishing. The personal info gathered helps the attacker disguise themselves and create an authentic-looking message that appears to come from a trusted. Learn About the Most Pervasive Types of Phishing and Prevention. Cybersecurity and its nature are constantly changing and several kinds of threats are evolving every now and.
Phishing Scams How To Recognize Avoid Them Sentinelone
Email-borne threats have always been a top priority for IT security but spear phishing is one of the fastest growing attacks. This can cause wide-ranging fraud and system security infiltration. One survey found that 72 of phishing sites were using digital certificates and TLS encryption just seeing HTTPS is no longer a guarantee of safety. In addition the practice of spear phishing is on the rise. Why Is Spear Phishing So Dangerous. Spear phishing is more precise. This phishing tactic learns of the victims personal information and uses it. According to CSO spear phishing attacks can be broken down into three main steps. Spear phishing requires more preparation and time to achieve success than a phishing attack. Because of their hyper-targeted nature spear phishing can be even more dangerous than traditional phishing.
Phishing attacks are easier to detect as they typically use more generic emails and are sent to large numbers of people. Understanding And Avoiding Spear Phishing and Phishing Attacks. Why is Spear-phishing the most harmful. The practice of hacking into someones system through emails shared through an already known contact of a person is known as spear phishing. This increased level of an understanding around a users interests is exactly what makes spear phishing so dangerous.
Pin On Work
Spear Phishing Leverages Zero-Day Exploits. Spear phishing is a type of phishing but more targeted. This can cause wide-ranging fraud and system security infiltration. Spear phishing attacks frequently rely on the delivery of malware via email. This phishing tactic learns of the victims personal information and uses it. One way to safely verify a link is by right-clicking on it and using the Inspect tool to check where its supposed to go. According to CSO spear phishing attacks can be broken down into three main steps. Instead they aim to access sensitive company data and trade secrets. In contrast spear-phishing is more dangerous because it focuses on an individual with personalized information. Spear phishing requires more preparation and time to achieve success than a phishing attack.
Firstly you need to know what is spear phishing. The familiar tone and content of a spear phishing message make it more difficult for the average user to detect heightening the threat level of this type of cyber attack. The purpose of the attack is the same as with any phishing email to gain access to login or confidential information or to deliver malware but in this instance the attack is targeted. Until they are fixed and patched they can be exploited by attackers to compromise systems and gain access to the network and other resources including personal and financial data. Spear-phishing attackers methodically target a victim to use them as a way into an organization or for stealing information while a phishing actor does not bother who their target is.
Phishing A Very Dangerous Cyber Threat Infosec Resources
The purpose of the attack is the same as with any phishing email to gain access to login or confidential information or to deliver malware but in this instance the attack is targeted. Personal information is used in spear-phishing attempts to construct convincing schemes. This is because spear phishing has a human touch. The practice of hacking into someones system through emails shared through an already known contact of a person is known as spear phishing. Phishing attacks are easier to detect as they typically use more generic emails and are sent to large numbers of people. Most early phishing was a mass attack the same email or recorded message sent to many people hoping to snag a minority of those contacted. Because of their hyper-targeted nature spear phishing can be even more dangerous than traditional phishing. A bad actor impersonates someone you trust in an effort to scam you or steal your information. This increased level of an understanding around a users interests is exactly what makes spear phishing so dangerous. Spear phishing is targeted phishing.
The familiar tone and content of a spear phishing message make it more difficult for the average user to detect heightening the threat level of this type of cyber attack. Spear phishing is a type of phishing but more targeted. As with regular phishing cybercriminals try to trick people into handing over their credentials. Spear phishing attacks frequently rely on the delivery of malware via email. Ad While Phishing Scams and Cyberthreats Are Constantly Evolving You Can Protect Yourself.
Why is Spear-phishing the most harmful. Most early phishing was a mass attack the same email or recorded message sent to many people hoping to snag a minority of those contacted. Spear phishing is targeted phishing. The dangers associated with spear phishing. Phishing attacks are easier to detect as they typically use more generic emails and are sent to large numbers of people. This increased level of an understanding around a users interests is exactly what makes spear phishing so dangerous. Spear phishing is more precise. One way to safely verify a link is by right-clicking on it and using the Inspect tool to check where its supposed to go. Why Is Spear Phishing So Dangerous. However the goal reaches farther than just financial details.






Post a Comment for "[High Resolution] Why Can Spear Phishing Be So Dangerous"
Post a Comment