Spear phishing tools - Spear Phishing Tools Spear Phishing Tools. These are the top benefits of spear phishing simulations. Share More sharing options. A spear phishing toolkit could include. Generates a fake pages to capture passwords. Top 10 Anti-Phishing Software in 2021. Up to 30 cash back Spear phishing attacks are designed to appear like legitimate emails from familiar or well-known sources. While there are a handful of classified phishing strategies the most common type of phishing attack is what experts call spear phishing. Spear phishing messages are often crafted with care using pernicious social engineering techniques and are difficult to defend against with mere technical means. Ad Take Your Online Phishing Recognition Training from Boring to Brilliant.
Area 1 Horizon Anti-Phishing Service. Spear phishing is a cyberattack method that hackers use to steal sensitive information or install malware on the devices of specific victims. Spear phishing attacks are targeted at. SlashNext Threat Labs observed a flurry of spear-phishing attacks targeting companies at the forefront of Covid-19 vaccines and therapeutics. Spear phishing is a targeted email attack purporting to be from a trusted sender. A recent report from iDefense Labs found that over 15000 corporate victims in the past 15 months have been hit by spear phishing attacks. 1 Filter Your Email and Implement Anti-Phishing Protection Besides traditional email security solutions such as anti-spam and antivirus filters extra anti-phishing software should be. 99997 threat detection efficacy. 1 day agoSpear PhishingWhile traditional phishing uses a spray and pray approach meaning mass emails are sent to as many people as possible spear phishing is a much more targeted. Zerospam is a competent cloud-based email filter that includes procedures for detecting phishing attempts.
Spearphisher A Simple Phishing Email Generation Tool
Spear phishing is a targeted email attack purporting to be from a trusted sender. SniperPhish helps to combine both. 1 Filter Your Email and Implement Anti-Phishing Protection Besides traditional email security solutions such as anti-spam and antivirus filters extra anti-phishing software should be. While there are a handful of classified phishing strategies the most common type of phishing attack is what experts call spear phishing. Zerospam is a competent cloud-based email filter that includes procedures for detecting phishing attempts. The most effective Cloud-Native Email Security. Spear Phishing Tools Spear Phishing Tools. Ad Stop Phishing BEC Attacks. Adds Targets Info to the The Fake Page. Cobalt Strikes spear phishing tool allows you to send pixel perfect spear phishing messages using an arbitrary message as a template.
Spear phishing tool using fake pages to capture user credentials. SlashNext Threat Labs observed a flurry of spear-phishing attacks targeting companies at the forefront of Covid-19 vaccines and therapeutics. Spear phishing is a targeted email attack purporting to be from a trusted sender. A recent report from iDefense Labs found that over 15000 corporate victims in the past 15 months have been hit by spear phishing attacks. Go to solution Solved.
Spear Phishing Cobalt Strike
These are the top benefits of spear phishing simulations. SlashNext Threat Labs observed a flurry of spear-phishing attacks targeting companies at the forefront of Covid-19 vaccines and therapeutics. Generates a fake pages to capture passwords. Cobalt Strikes spear phishing tool allows you to send pixel perfect spear phishing messages using an arbitrary message as a template. Spear phishing tool using fake pages to capture user credentials. Get a Free Trial. Adds Targets Info to the The Fake Page. SniperPhish helps to combine both. 1 Filter Your Email and Implement Anti-Phishing Protection Besides traditional email security solutions such as anti-spam and antivirus filters extra anti-phishing software should be. Spear phishing attackers typically attempt to impersonate a trusted individual such as a company CEO or manager to extract information from a target.
99997 threat detection efficacy. The new Lunker phishing attack and. A spear-phishing attack using SET allows us to craft and send email addresses to either a single person or a group of people with malicious payloads attached. Top 10 Anti-Phishing Software in 2021. Ad While Phishing Scams and Cyberthreats Are Constantly Evolving You Can Protect Yourself.
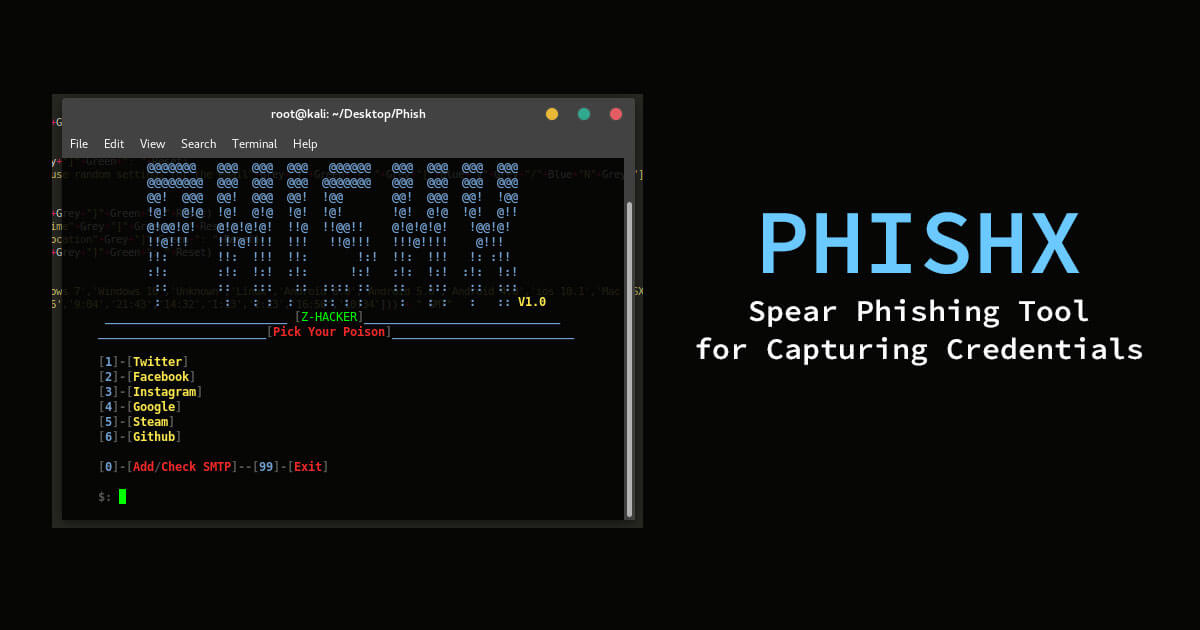
Phishx Spear Phishing Tool For Capturing Credentials Latest Hacking News
Secure Microsoft 365 GSuite emails. Anatomy of a Spear Phishing Attack. SniperPhish is a phishing toolkit for pentesters or security professionals to enhance user awareness by simulating real-world phishing attacks. Spear phishing is a cyberattack method that hackers use to steal sensitive information or install malware on the devices of specific victims. Adds Targets Info to the The Fake Page. Deploying AI models to help create their spear phishing attacks. Phishing Attacks Aim to Steal or Damage Sensitive Data by Deceiving People. Get a Free Trial. A spear-phishing attack using SET allows us to craft and send email addresses to either a single person or a group of people with malicious payloads attached. Ad While Phishing Scams and Cyberthreats Are Constantly Evolving You Can Protect Yourself.
A spear phishing toolkit could include. Sends SMSs using services like FacebookInstagramGoogle. By Seb1 November 3 2021 in Social Engineering NLP. The new Lunker phishing attack and. Spear phishing is a targeted email attack purporting to be from a trusted sender.
Spear Phishing Attack An Overview Sciencedirect Topics
1 Filter Your Email and Implement Anti-Phishing Protection Besides traditional email security solutions such as anti-spam and antivirus filters extra anti-phishing software should be. Generates a fake pages to capture passwords. While there are a handful of classified phishing strategies the most common type of phishing attack is what experts call spear phishing. SniperPhish is a phishing toolkit for pentesters or security professionals to enhance user awareness by simulating real-world phishing attacks. Phishing Attacks Aim to Steal or Damage Sensitive Data by Deceiving People. After identifying a target individual or. Top 10 Anti-Phishing Software in 2021. The new Lunker phishing attack and. In spear phishing attacks attackers often use information gleaned from research to put the. These are the top benefits of spear phishing simulations.
A spear phishing toolkit could include. Heres an example of spear phishing vs. AI tools are inevitably getting more leveraged by fraudsters. Spear phishing messages are often crafted with care using pernicious social engineering techniques and are difficult to defend against with mere technical means. Overview Area 1 Horizon is a cloud-based service that offers protection from phishing on the.
Spear Phishing Attack Prevention Cyber Security Tool Slashnext
This service prevents malicious emails of all types from even. Spear phishing tool using fake pages to capture user credentials. Spear phishing is a targeted email attack purporting to be from a trusted sender. Spear Phishing Tools Spear Phishing Tools. By Seb1 November 3 2021 in Social Engineering NLP. AI tools are inevitably getting more leveraged by fraudsters. Measure the degree of corporate and employee vulnerability Teach employees to recognize harmful malicious. Top 10 Anti-Phishing Software in 2021. Overview Area 1 Horizon is a cloud-based service that offers protection from phishing on the. Learn how to recognizeand defeatthis type of phishing attack.
The new Lunker phishing attack and. There is also functionality. Zerospam is a competent cloud-based email filter that includes procedures for detecting phishing attempts. 1 day agoSpear PhishingWhile traditional phishing uses a spray and pray approach meaning mass emails are sent to as many people as possible spear phishing is a much more targeted. A recent report from iDefense Labs found that over 15000 corporate victims in the past 15 months have been hit by spear phishing attacks.
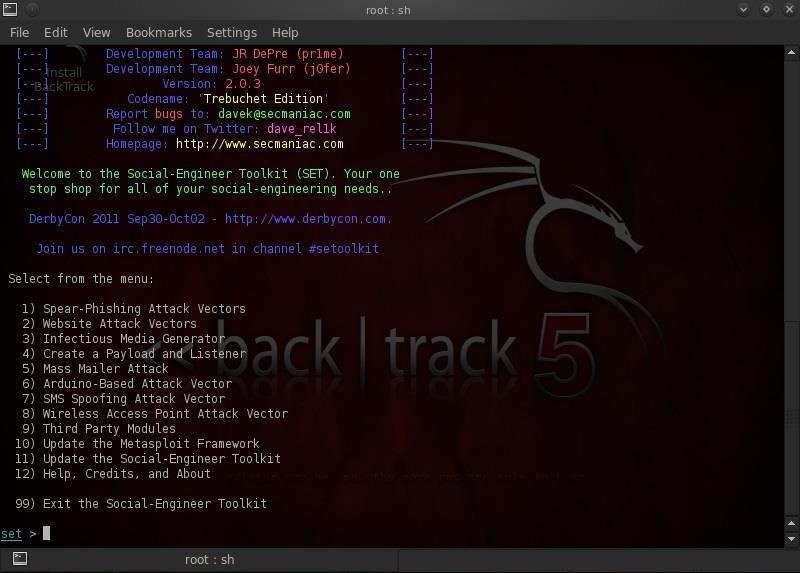
Creating A Spear Phishing Attack With The Social Engineering Toolkit Kali Linux 2 Windows Penetration Testing Book
Spear phishing is a cyberattack method that hackers use to steal sensitive information or install malware on the devices of specific victims. Anatomy of a Spear Phishing Attack. Top 10 Anti-Phishing Software in 2021. Generates a fake pages to capture passwords. This service prevents malicious emails of all types from even. After identifying a target individual or. Area 1 Horizon Anti-Phishing Service. Adds Targets Info to the The Fake Page. Get a Free Trial. Targets Before you send a phishing message you.
Ad While Phishing Scams and Cyberthreats Are Constantly Evolving You Can Protect Yourself. Spear Phishing Tools Spear Phishing Tools. SlashNext Threat Labs observed a flurry of spear-phishing attacks targeting companies at the forefront of Covid-19 vaccines and therapeutics. A spear-phishing attack using SET allows us to craft and send email addresses to either a single person or a group of people with malicious payloads attached. Heres an example of spear phishing vs.
Hack Like A Pro How To Spear Phish With The Social Engineering Toolkit Set In Backtrack Null Byte Wonderhowto
These are the top benefits of spear phishing simulations. Spear phishing is a targeted email attack purporting to be from a trusted sender. A spear phishing toolkit could include. A spear-phishing attack using SET allows us to craft and send email addresses to either a single person or a group of people with malicious payloads attached. Spear phishing is a targeted email attack purporting to be from a trusted sender. Generates a fake pages to capture passwords. SniperPhish helps to combine both. This service prevents malicious emails of all types from even. A request from a colleague coming from an email with their actual name asking for specific. Spear phishing attacks are targeted at.
Phishing Attacks Aim to Steal or Damage Sensitive Data by Deceiving People. Deploying AI models to help create their spear phishing attacks. The new Lunker phishing attack and. Cobalt Strikes spear phishing tool allows you to send pixel perfect spear phishing messages using an arbitrary message as a template. 99997 threat detection efficacy.
How To Protect From Corporate Spear Phishing In 2022 Plus Tools
1 day agoSpear PhishingWhile traditional phishing uses a spray and pray approach meaning mass emails are sent to as many people as possible spear phishing is a much more targeted. While there are a handful of classified phishing strategies the most common type of phishing attack is what experts call spear phishing. Sends SMSs using services like FacebookInstagramGoogle. Adds Targets Info to the The Fake Page. Anatomy of a Spear Phishing Attack. Share More sharing options. A request from a colleague coming from an email with their actual name asking for specific. Overview Area 1 Horizon is a cloud-based service that offers protection from phishing on the. Area 1 Horizon Anti-Phishing Service. Go to solution Solved.
Spear phishing is a targeted email attack purporting to be from a trusted sender. Generates a fake pages to capture passwords. Deploying AI models to help create their spear phishing attacks. Spear Phishing Tools Spear Phishing Tools. SlashNext Threat Labs observed a flurry of spear-phishing attacks targeting companies at the forefront of Covid-19 vaccines and therapeutics.
Uftp Udp Based Ftp With Encryption Hacking Tools Isoeh
A request from a colleague coming from an email with their actual name asking for specific. This service prevents malicious emails of all types from even. AI tools are inevitably getting more leveraged by fraudsters. These are the top benefits of spear phishing simulations. Sends SMSs using services like FacebookInstagramGoogle. Zerospam is a competent cloud-based email filter that includes procedures for detecting phishing attempts. Up to 30 cash back Spear phishing attacks are designed to appear like legitimate emails from familiar or well-known sources. Area 1 Horizon Anti-Phishing Service. Secure Microsoft 365 GSuite emails. Ad While Phishing Scams and Cyberthreats Are Constantly Evolving You Can Protect Yourself.
Learn how to recognizeand defeatthis type of phishing attack. Generates a fake pages to capture passwords. SniperPhish is a phishing toolkit for pentesters or security professionals to enhance user awareness by simulating real-world phishing attacks. Targets Before you send a phishing message you. Measure the degree of corporate and employee vulnerability Teach employees to recognize harmful malicious.
The Top 10 Phishing Protection Solutions Expert Insights
Get a Free Trial. 99997 threat detection efficacy. Ad Stop Phishing BEC Attacks. Ad While Phishing Scams and Cyberthreats Are Constantly Evolving You Can Protect Yourself. Share More sharing options. Phishing Attacks Aim to Steal or Damage Sensitive Data by Deceiving People. The most effective Cloud-Native Email Security. Spear phishing tool using fake pages to capture user credentials. Top 10 Anti-Phishing Software in 2021. Heres an example of spear phishing vs.
Spear phishing attacks are targeted at. Generates a fake pages to capture passwords. Cobalt Strikes spear phishing tool allows you to send pixel perfect spear phishing messages using an arbitrary message as a template. Up to 30 cash back Spear phishing attacks are designed to appear like legitimate emails from familiar or well-known sources. This service prevents malicious emails of all types from even.
Generates a fake pages to capture passwords. This service prevents malicious emails of all types from even. A recent report from iDefense Labs found that over 15000 corporate victims in the past 15 months have been hit by spear phishing attacks. 99997 threat detection efficacy. Area 1 Horizon Anti-Phishing Service. Ad Take Your Online Phishing Recognition Training from Boring to Brilliant. A request from a colleague coming from an email with their actual name asking for specific. Zerospam is a competent cloud-based email filter that includes procedures for detecting phishing attempts. Spear Phishing Tools Spear Phishing Tools. Phishing Attacks Aim to Steal or Damage Sensitive Data by Deceiving People.






No comments